IoT & Embedded Technology Blog
Security of Things Hackathon

Fresh on the heels of successful adventures in Spain (MWC), Germany (embedded world), and San Francisco (RSA), VDC found itself a bit closer to home last weekend at the MIT-hosted Security of Things conference and hackathon. A wide range of programmers, academics, IT professionals, researchers, engineers, and students gathered in the gleaming glass and steel atrium of the MIT Media Lab in order to talk, eat, joke, learn, and hack. The goal of the event? To promote awareness of common IoT threats, review tools for building more secure, transparent devices, and walk through the (surprisingly simple) process of compromising devices that are used in millions of homes today.

Security guru Bruce Schneier opened up the conference with a high-level discourse on his view of the IoT as The World’s Biggest Robot. He argues that the Internet is becoming the central nervous system of a robot with connected end nodes that will both monitor and control many facets of our lives. He highlighted the importance of vendor responsibility (a recurring theme throughout the day) as well as the need for a new “Government Department of Technology Policy” in order to combat the short-sighted security incentives of the private market. The talk set up a great framework for thinking about the importance of the IoT on a global scale and raised some interesting questions from the crowd.
Mikko Varpiola, a security expert with Synposys, spoke next. He began by clearly illustrating the point that software is no longer written, it is assembled. Today’s software engineers write code to string together a collection of disparate operating systems, libraries, drivers, frameworks, and applications, ending up with a complicated and opaque software stew. Consequently, a vulnerability in Component X within Library Y buried in Subsystem Z might go unnoticed. Varpiola sampled a wide range of consumer electronics devices, finding 3 third party components per device on the low end (infusion pump), up to 133 third party components in a modern smartphone. Security issues will only multiply over time as hardware continues to outlive software update cycles.

So what was his proposed solution to the complexity of modern software development and maintenance? BOMtotal – a website that takes in an application file and breaks it into all of its different components, outputting a BOM (bill of materials) in human readable form that looks much like the nutrition and ingredients labels that are mandated by the FDA for edible goods. The BOM would list version type and license, making it easy to evaluate the end product against known vulnerability databases and keep track of license requirements introduced by different components.
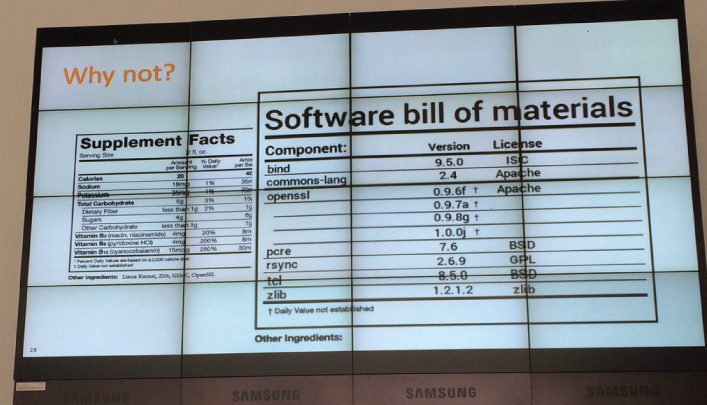
Courtesy of Markus Schrober (@mascho) on Twitter.
After these talks and a quick chat with tablemates over lunch, the event organizers handed out of a wide range of IoT consumer devices. Participants opened up laptops, wrestled cables and cords into crowded power outlets, and a low buzz of tapping-punctuated dialogue settled over the room. Within a few minutes, some of the groups had successfully located firmware files for their devices and began running the code through binary analysis tools to check for vulnerabilities. It was fascinating to see just how easy modern tools made the vulnerability mapping process. Organizers informed us that we would not be able to keep the hacked devices, but joked that they would be returning them to the stores where they had been purchased – quite an unsettling idea the more one thinks about it.

Courtesy of Ofer Maor (@OferMaor) on Twitter.
Overall, the hackathon brought an interesting mix of people together, and served as a great platform for drilling down into concrete examples of how complicated and vulnerable today’s connected devices can be. Our main takeaway is that the three crucial players – the government, the private sector, and the consumer – must continue to actively push against each other and make responsible, informed demands if the IoT is to move forward. As Schneier says, “We don’t have a choice between government and no government. Just smarter government and stupider government.” Likewise, consumers and embedded vendors will need to deal in shades of gray with respect to security, usability, transparency, and cost tradeoffs. We look forward to seeing progress on IoT security as the market matures, and hackathons such as the Security of Things 2016 introduce tools, best practices, and design paradigms to a rapidly-evolving ecosystem.
View the 2017 IoT & Embedded Technology Research Outline to learn more.