Enterprise Mobility & the Connected Worker Blog
Business Benefits Crucial to Wearables
VDC’s mobile team recently published its annual security report. The Report, titled “Mobility Spurs Security Ecosystem Expansion”, details how the adoption of mobility in corporate setting has—for all intents and purposes—blown up the notion of a corporate network perimeter. Threats now extend much further than devices: vulnerabilities, such as malware, direct attacks, data interception, exploitation, and social engineering are all evolving and remain a threat on endpoints in our hands, at our desks, on our networks, and within the data centers of our service providers.
Our research showed an uptick in the number of companies that are engaging with third parties for consultation, services, and technology to improve their security posture and hygiene, specifically in the areas of intrusion detection and incident response. However, as depicted below, there are many factors that are (and will continue to) contribute to the demise of the perimeter.
The Demise of the Perimeter
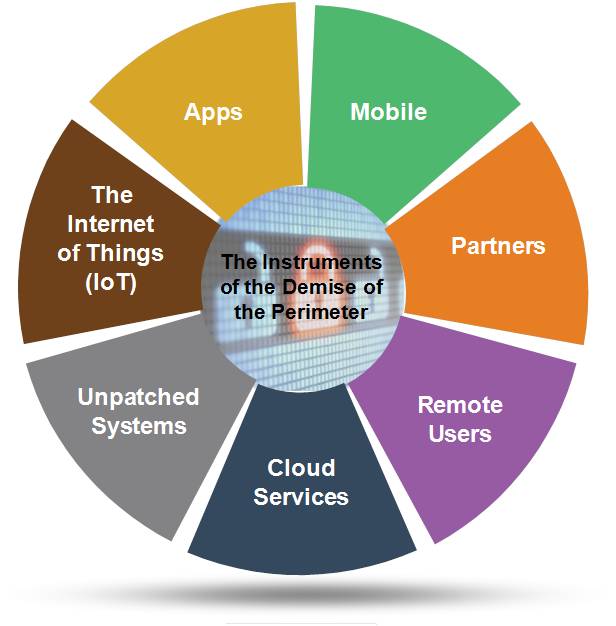
These elements are weakening the security postures of even the most aggressive investors in mobile and data security. This is primarily due to the shifts in how most of us now work and conduct business, both internally and externally, with our partners and customers. Due to degradation of the perimeter, organizations should now shift their focus to:
- Documenting their application portfolios and conducting application assessments
- Conducting application security threat assessments on a regular cadence
- Auditing their security postures on a quarterly basis
- Ensuring that retirement plans are in place for existing solutions which are being sunsetted
- Evaluating and experimenting with modern security solutions which focus on application and cloud security
- Increasing investment in educating their end-users on security hygiene
- Revisiting their application security and endpoint management strategies and speaking with their primary vendor(s)
EMM Not Enough
Most enterprises have rightly focused on securing the smartphones and tablets they support as they deploy new mobile applications and further leverage mobile solutions to modernize and elevate mobility’s role in their organizations. EMM solutions have clearly helped, but organizations must do more and accept that their investments in these deployments are just the first steps in the evolution of their security infrastructures. In fact, our data showed that 39% of large organizations (>1,000 employees) have deployed an EMM solution; however, many companies have yet to expand their solution beyond basic mobile device management (MDM). EMM vendors are competing very well with traditional security vendors (e.g., IBM, Intel Security, Palo Alto Networks, and Symantec) by successfully partnering and integrating with a broad spectrum of best-of-breed security vendors. EMM vendors have been effective in leveraging their mobile-first acumen/mindset, brand strength, and large enterprise customer bases and are clearly being more aggressive and speedy in forging these partnerships. The partnerships are helping EMM vendors pivot to security solution providers; but enterprises have to go further, as their users’ behavior continues to evolve and their application range expands.
- Cyber threats have quickly become a critical issue affecting the national security in every major industrial country worldwide. The rise of cloud computing and big data, and the sometimes unclear virtual boundaries caused by mobile enterprises are key contributing factors.
- Mobile enablement introduces threats to enterprise IT that cannot be offset, mitigated, or prevented by a single technology solution. Combating those threats requires a layered approach to security to ensure the protection of corporate data.
- As organizations continue to pursue and expand their mobile initiatives, they should identify and incorporate endpoint management solutions that ensure the security and reliability of both their traditional endpoints (e.g., desktops and notebooks), modern mobile platforms (e.g., smartphones and tablets), and IoT devices.
- Most organizations use a combination of usernames, passwords, digital certificates, and multi-factor devices to authenticate users of cloud-based services (depending on the application/device). So, while a typical organization may already have a single sign-on solution, integration work remains, as the number of devices and cloud applications being used continues to expand.
- The security ecosystem continues to expand due to a greater reliance on mobility and cloud applications in corporate settings. This expansion has led to a crowded, competitive, and fragmented security ecosystem with robust venture funding and increasing merger and acquisition activity.
- Vendors participating in the market for endpoint management solutions are clearly demarcated between mobile-first enterprise mobility management (EMM) who are attempting to transition to security firms, and tenured traditional endpoint management vendors that have only recently begun to augment their solutions with mobility management features.
- While 84 percent of end-users/survey respondents see value in a unified endpoint management solution (UEM), few are actively sourcing/deploying UEM solutions. The opportunity to manage heterogeneous mobile platforms alongside traditional PC deployments through a single pane of glass is real and can help to reduce costs, allow for consistent policy enforcement, and free up IT staff to work on other more business-critical initiatives.
- Modern operating systems, such as Apple’s macOS and Microsoft’s Windows 10, have created an opportunity for security vendors to participate in the market for next-generation UEM solutions—however, traditional endpoint vendors are coming from the opposite direction and expanding their mobile solution range.
- Educating employees is critical to minimizing the threats mobile enablement introduces to an IT infrastructure. Typical users either don’t understand the available security mechanisms or cannot properly use the appropriate protection mechanisms to their (and their organization’s) full benefit. For this reason, education budgets should be expanded to ensure that continuing education for security-specific education initiatives are covered.
Vendors that we profiled in our report included: Apperian, Arxan, Better, Bitglass, BlackBerry, Blue Cedar Networks, Citrix, Entrust, IBM, Microsoft, Netskope, Okta, Oracle, Proofpoint, Pulse Secure, Samsung, Signal Sciences, Vera, VMware/AirWatch, Zimperium, and Zscaler. We also profiled several IoT Security vendors, these included: Bastille, Intel Security (McAfee), Mocana, and Wurldtech.
View the 2017 Enterprise Mobility & Connected Devices Research Outline to learn more.