IoT & Embedded Technology Blog
SBOMs & the Shifting IoT Regulatory Landscape
by Joe Abajian | 9/26/2023
Cybersecurity concerns loom over the increasingly targeted healthcare sector and other connected industries. Attacks can cost health networks millions of dollars and compromise patient care. Beyond healthcare, downtime of manufacturing lines, utilities, and other connected infrastructure can be devastating. As a result, law makers, industry participants, and standards organizations and consortia are rapidly shaping IoT’s security future. Across the United States and Europe, regulators have bolstered embedded device security requirements. Yet the question remains—can recent regulations guarantee impregnable devices and networks?
A consistent requirement in legislation addressing embedded device security is the inclusion of a Software Bill of Materials (SBOM). An SBOM includes every software component used in an embedded device. Its purpose is to expose vulnerable components in the software supply chain that would otherwise be left unexamined. Across the broader IoT regulatory landscape, SBOMs have become a popular requirement alongside more general cyber security guidelines.
In the United States, the Consolidated Appropriations Act (2023) requires that all medical "cyber devices" contain an SBOM as of March 29th, 2023. A cyber device is any device that connects to the internet or has components vulnerable to cyber-attacks. If manufacturers fail to comply, they risk a "Refuse to Accept" rating from the FDA, which excludes them from the market. Executive Order 14028 (2021) requires all federally used and purchased embedded devices to provide an SBOM. Both policies will trigger ripple effects across adjacent markets.
Regulations in the European Union are less solidified but more stringent. The Cyber Resiliency Act (CRA) was sent to the European Parliament after passing in the Council of the European Union. The act requires baseline security measures for all IoT devices. One measure is the inclusion of an SBOM in every connected device . If manufacturers fail to meet standards, they will face a penalty of 15,000,000 EUR or 2.5% of the previous year's revenue (whichever is higher).
Lawmakers have attached substantial stakes to software security and SBOMs. Failing to meet requirements could permanently damage a manufacturer's competitive standing. Guideline adherence is of utmost strategic importance to OEMs.
Regardless of legal gravity, are SBOMs the cyber security silver bullet regulators dream of? No. Not yet. Even if every device had an SBOM, most SBOMs fail to adhere to a standard format. Many are manually generated and contain errors. The Consolidated Appropriations Act (2023) and CRA reserve the right to further define what is contained in an SBOM, but do not list explicit terms. Existing SBOM standardization and generation tools lack exposure and integrability, leaving OEMs in search of reliable security partners.
The next steps for OEMs attempting to navigate regulations (and potentially gain a competitive advantage by complying with them) are clear.
OEMs must scrutinize their SBOMs and SBOM generation methods. In-house software supply chains should never contain documentation errors. Manual SBOM generation should be avoided in favor of standards based SBOM generators like CycloneDX, FOSSA, or NXP Vigiles, which read component metadata during processing, remove the risk of human error, and identify dependencies and licenses in real time. Different Software Composition Analysis (SCA) tools provide unique advantages. Synopsys, for example, specializes in IoT security and services, offering OEMs penetration testing, static application security testing, and software securitization training.
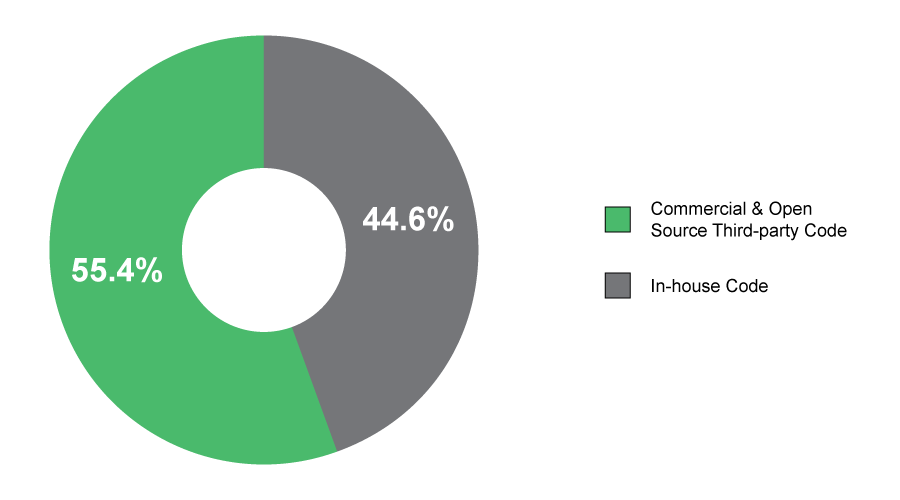
Third-party software inclusion puts embedded projects at risk. Due to the lack of universally accepted SBOM standards, many third-party vendors fail to meet documentation benchmarks. According to VDC’s Voice of the Engineer Survey, the majority of software (55.4%) comes from third-party sources (see Exhibit 1). Without vetting third-party SBOM methodology, OEMs risk supply chain vulnerabilities. OEMs should require off-the-shelf software to meet SPDX guidelines, which is the only ISO recognized SBOM standard. Homogenizing documentation methodology across the supply chain is the best way for OEMs to avoid regulatory consequences and produce secure devices.
Exhibit 1: Percent of Total Software Code in Final Design of Current Project
For a comprehensive list of SCA providers, data, and market analytics, read VDC’s 2023 report, The Global Market for Software Composition Analysis 2021 to 2026.