IoT & Embedded Technology Blog
IoT Use Cases for Enigma & Homomorphic Encryption
Homomorphic encryption is a method of encryption that allows computations to be performed upon fully encrypted data, generating an encrypted result that, after decryption, will match the result of the desired operations on the plaintext, decrypted data. In other words, homomorphic encryption allows a user to manipulate data without needing to decrypt it first.
Daniele Micciancio states the problem that is solved by homomorphic encryption in a 2010 journal article entitled A First Glimpse of Cryptography’s Holy Grail:
Using standard encryption technology we are immediately faced with a dilemma: either we store our data unencrypted and reveal our precious or sensitive data to the storage/ database service provider, or we encrypt it and make it impossible for the provider to operate on it.
If data is encrypted, then answering even a simple counting query (for example, the number of records or files that contain a certain keyword) would typically require downloading and decrypting the entire database content.
IBM has shown the most interest in the development of this space thus far, presumably to bolster the security of its burgeoning cloud business. In October 2013 it was granted a patent entitled Efficient implementation of fully homomorphic encryption, but the use cases for the patent technology were limited, and IBM has been silent on its implementation of the technology since then.
Enigma
MIT Researchers Guy Zyskind and Oz Nathan, advised by Professor Alex “Sandy” Pentland, have recently announced a project dubbed Enigma that makes a major conceptual step towards this “Holy Grail” of a fully homomorphic encryption protocol. From the white paper's abstract:
A peer-to-peer network, enabling different parties to jointly store and run computations on data while keeping the data completely private. Enigma’s computational model is based on a highly optimized version of secure multi-party computation, guaranteed by a verifiable secret-sharing scheme. For storage, we use a modified distributed hashtable for holding secret-shared data. An external blockchain is utilized as the controller of the network, manages access control, identities and serves as a tamper-proof log of events. Security deposits and fees incentivize operation, correctness and fairness of the system. Similar to Bitcoin, Enigma removes the need for a trusted third party, enabling autonomous control of personal data. For the first time, users are able to share their data with cryptographic guarantees regarding their privacy.
Use Cases
If Enigma is implemented properly, it could have a sizable impact on the way that many companies in data-sensitive industries (such as healthcare, insurance, and finance) store and interact with their customer’s data.
Enigma’s major disadvantage comes in the form of increased time and power (money) to perform these computations as distributing and operating on encrypted data is more complex than computing over plaintext. Enigma makes computation across a large number of nodes much more efficient than previous methods of multi-party homomorphic encryption, but it is still at least 20x slower than plaintext computation.
Again, we are faced with the classic tradeoff between cost and security.
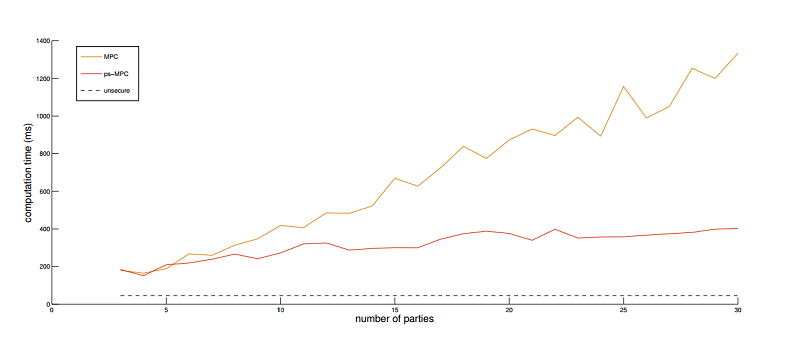
"Simulated performance comparison of [Enigma's] optimized secure MPC [multi-party computation] variant compared to classical MPC." Source: Figure 4, Enigma Whitepaper.
There are currently a limited number of use-cases that we can conceptualize, but demand is likely to come from companies in industries with heavy government regulations regarding data privacy.
One use case would be for interactions between hospitals and health-care providers who store encrypted patient data as per HIPAA regulations, and the research & pharmaceutical companies that would benefit from access to this data for clinical analysis. Let us imagine that Hospital X is generating large amounts of sensitive medical data. Following industry best practices under HIPAA regulations, the hospital uses AES-256 to encrypt the data, and then stores it in the cloud. BigPharma, InsuranceCo, and University Y approach Hospital X, asking for permission to access and analyze the data.
Traditionally, Hospital X would have been required to first decrypt, then anonymize the data before granting access to a partner. Each of these additional steps is time consuming, and introduces complexity which increases the risk of compromising the data. With Enigma, Hospital X performs no operations on the data; it only decides whether or not to grant its partners access to the encrypted data.
Let us say that Hospital X grants University Y access to the encrypted data. Researchers from University Y specify the operations that they wish to perform on the data. Enigma then breaks the encrypted data into smaller chunks. Each chunk is processed by a separate computer, called a node. This method of problem solving is known as decentralized computing.
The benefits of decentralization are twofold: Firstly, if one node fails or aborts the computation prematurely, the other nodes can pick up and process the dropped computation. Secondly, if one node is compromised, the malicious agent will only have access to a meaningless portion of the data, and will not be able to reconstruct the entire dataset. As long as a majority of nodes are “good” (functioning and uncompromised), the computation remains flexible and secure. University Y obtains the final product without ever needing to access or handle Hospital X’s unencrypted data.
The scenario described above would be more expensive than simply trusting a third party compute solution, but it could be beneficial for a consumer-facing company’s reputation, or even mandated by the government as an addition to HIPAA or the Fair Credit Reporting Act (FCRA).
Conclusion
Zyskind and Nathan suggest that Enigma could be used to “store, manage and use (the highly sensitive) data collected by IoT devices in a decentralized, trustless cloud.” How exactly the concepts of homomorphic encryption and secure multi-party computation might play out in the IoT and embedded systems space remains to be seen, but it is an exciting development in an industry whose future is tied directly to advances in security and privacy techniques.
Needless to say, we at VDC Research will be keeping an eye on Enigma, as its source code and scripting language will be released near the end of the summer.
View the 2019 IoT & Embedded Technology Research Outline to learn more.